Set up ProCall securely for productive use
June 2025
ProCall on-premises
- ProCall 8 Enterprise
- ProCall Infinity (DataCenter)
- MetaDirectory
ProCall Enterprise and ProCall DataCenter offer extensive setting options for secure communication.
To enable you to make the appropriate settings, we have summarised the key points for the procedure here.
For productive environments ,it is strongly recommended that you make these settings (such as the TLS setup ) .
You shouldactivate the corresponding encryption methods at the latest when you switch from test operation to productive operation with real data.
ProCall NEX (Cloud)
With ProCall NEX, transport encryption such as TLS is already included in the estos cloud solution. You do not need to make any settings in the UCServer.
Prerequesite
Valid TLS certificate
You need a valid TLS certificate together with the corresponding private key either from a public certification authority or from your Enterprise CA.
Windows certificate management - own certificates
The certificate must be available in the Microsoft Windows operating system in the certificate management of the Microsoft Management Console (MMC), under own certificates .
Example screenshot: Manage computer certificates - Certificates (local computer) - Own certificates - Certificates of the UCServer computer
PFX file and PEM file
You also need a corresponding PKCS#12 (.pfx) file and .pem file containing the certificate and the private key.
Settings in the UCServer
You can activate TLS:
- either directly during the installation from the setup dialogue "Network interfaces"
- or later in the UCServer administration under Extras - Network settings
You must make the settings for activating the encryption and importing the certificate individually for each type (port) .
Example screenshot UCServer Administration - Extras - Network interfaces
Open the properties of the interfaces and activate the certificate there.
Here is what it looks like after a simple installation:
Example screenshot of network interfaces - Configuring network interfaces - no encryption
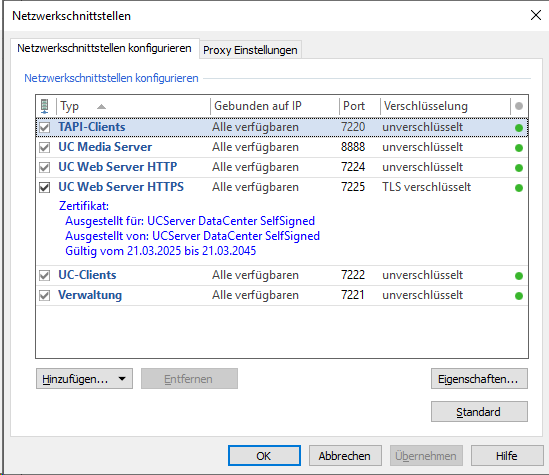
For productive operation, the interfaces should be secured as follows:
Example screenshot of network interfaces - Configuring network interfaces - activated encryption
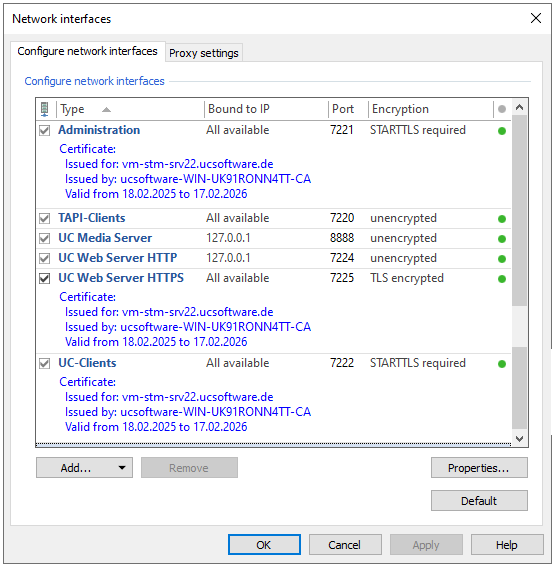
Dazu aktivieren Sie für jede Schnittstelle eigens die Verschlüsselungsmethode mit Zertifikat oder binden diese an den Computer:
Typ
- Administration, Port 7221
- This is the interface of the UCServer administration client. As this may also be used from other computers, activate TLS here and set the certificate.
- TAPI-Clients, Port number 7220
- This is the interface for the remote or Multiline TAPI driver. If you do not need this, you can remove the tick at the front (switch it off). Otherwise, activate TLS and set the certificate here too.
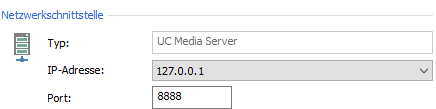
- UC Media Server, Port 8888
- As a rule, the UC Media Server in ProCall Enterprise is only operated locally on the same machine as the UCServer.
Therefore, bind this port to "localhost" (127.0.0.1). TLS is then not necessary and does not require any additional resources. - With ProCall Infinity (DataCenter) and several media servers, you should configure the corresponding ports for TLS with certificate.
- As a rule, the UC Media Server in ProCall Enterprise is only operated locally on the same machine as the UCServer.
- UC Web Server HTTP, Port 7224
- For secure operation, bind this interface to localhost (127.0.0.1).
Do not deactivate this, as the UCWeb might no longer be accessible if there is a problem with the certificate (possibly expired). This means that it can still be accessed from localhost in the event of a problem.
- For secure operation, bind this interface to localhost (127.0.0.1).
- UC Web Server HTTPS, Port 7225
- This interface is also equipped with a certificate for a simple installation.
However, this should be replaced by your own certificate , as self-signed certificates are not classed as secure.
- This interface is also equipped with a certificate for a simple installation.
- UC-Clients, Port 7222
- This is the interface for the ProCall clients for Windows. This should definitely be configured to TLS with certificate again.
Setting up TLS and certificates
Double-click on the respective network interface or simply click on "Properties..." to open the dialogue for the settings.
Example UC client, for all network interfaces and enforce TLS
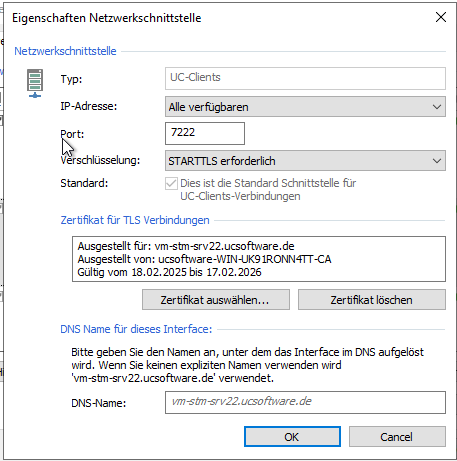
To set up a TLS connection with a certificate, you must perform the following steps:
- Leave "All available" under "IP address:".
- Set "Encryption:" to "STARTTLS required" or "TLS encrypted" (if available).
- Click " Select certificate..." under "Certificate for TLS connections" and select the certificate set up in the Windows certificate management in the system dialogue for certificates that appears.
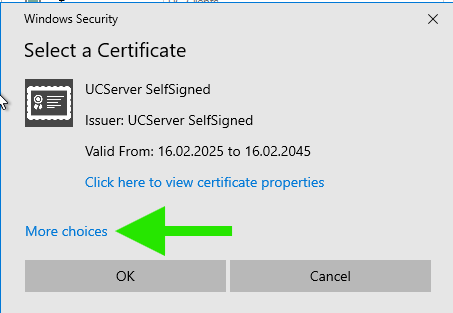
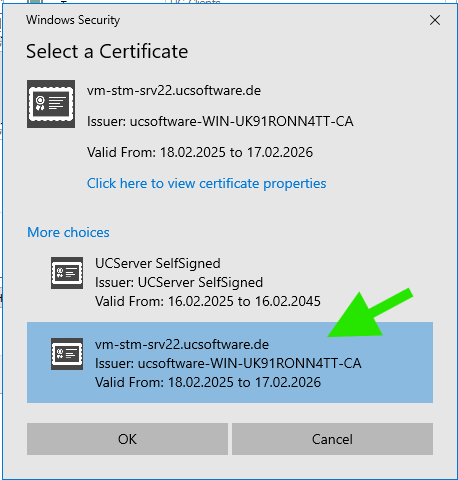
Confirm the system dialogue and the properties dialogue with "OK" and click on "Apply" in the network interface overview.
After a short time, the light on the far right for the interface should be green again.
Bind to localhost
If you only want to bind an interface to "localhost" (127.0.0.1), select the address "127.0.0.1" from the drop-down menu under "IP address:" .
Example UC Media Server
Media Server and UC Web Server HTTPS
Setting up TLS with a certificate for Media Server and UC Web Server HTTPS has the special feature that the certificate must be available in the PKCS#12 (.pfx) file or .pem file.
In this case, use "Select certificate..." to open a file explorer, which you can use to search for and select this file.
Example Search for and select certificate file .pfx
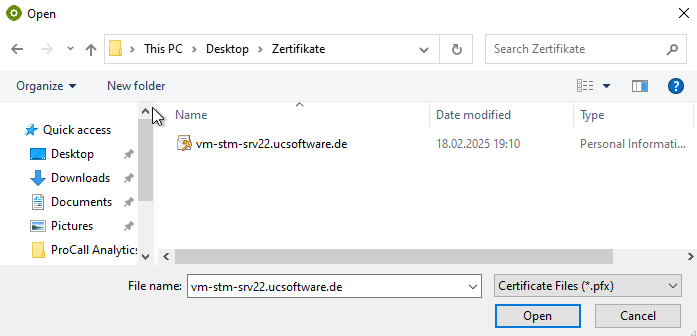
You may now be asked to enter the password for the certificate.
Then confirm again with "OK", "Apply" and check whether the green light is active again.
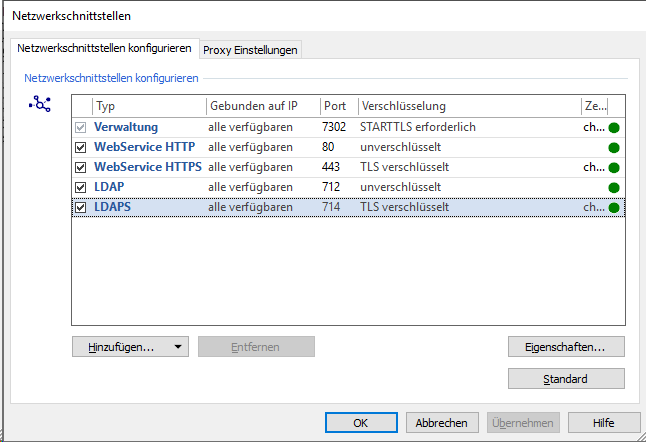
Settings in the MetaDirectory Administrator
Example screenshot MetaDirectory Administrator - Extras - Network interfaces
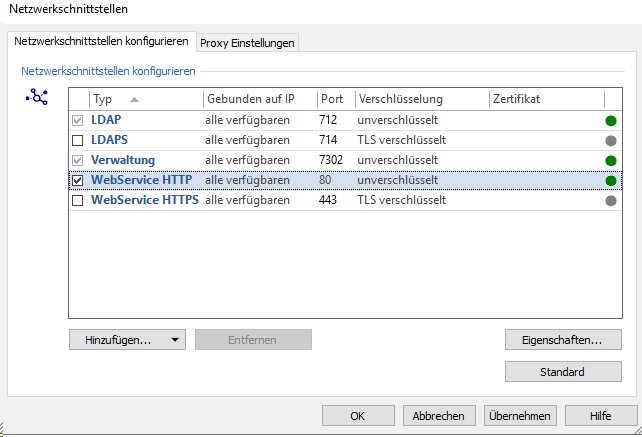
You have to change the encryption settings for the following types (ports) :
- LDAPS
- WebService HTTPS
- Administration
For the typeLDAPSandWebService HTTPS , activate the encryption from unencrypted to TLS encryptedand select the certificate.
Example screenshot MetaDirectory network interfaces - Type: LDAPS/WebService HTTPS - Encryption unencrypted → TLS encrypted
Whether WebService HTTP can be switched off depends on other connected clients.
For the Administration type, change the encryption from unencrypted to START-TLS and select the certificate.
Example screenshot MetaDirectory network interface type - Result of the changeover: Encryption for LDAPS, WebService HTTPS and administration activated
Further information
Release ports for estos products – which network interfaces are used?
Disabling insecure encryption protocols (TLS1.0/TLS1.1)
Supported cryptographic algorithms (ciphers)
Login to ProCall
ProCall Web - Login options