Use custom app registration
May 2022
ProCall 7 Enterprise from version 7.4.2
Please note that estos cannot provide support on the maintenance of a custom app registration. For a quick and easy way of starting up, please proceed as described in ProCall integration in Microsoft Teams and use the company app estos ProCall integration in Teams.
Background
ProCall Integration in Microsoft Teams describes how to set up and use it. estos provides a separate custom app (estos ProCall integration in Teams) for this purpose.
If you do not want to use this app provided by estos, but instead want to register an app for the company yourself, then proceed as follows:
Implementation
The steps described here must take place before you can Start-up ProCall integration in Microsoft Teams.
Create an app registration
Please refer to the official Microsoft Documentation for details. Only the absolutely necessary steps are described here. These may differ depending on the Azure client.
- Login to the Azure Portal with appropriate permissions to create app registrations in your tenant.
- Go to "Azure Active Directory" → "App Registration" and create a new registration.
- Assign a unique name and specify which clients are allowed to access the app registration.
- Set the following as the "Redirect URI":
"Public client/native (mobile and desktop)" "http://localhost"- Optionally: "Public client/native (mobile and desktop)" "https://www.estos.de/piimt"
This optional URL is not necessary, but only cosmetic, if the "admin consent" is to be assigned again via the UCServer administration. This URL is only a help page that the "admin consent" was successful. In the instructions described here, however, it is described how the "admin consent" is carried out directly via the Azure portal and therefore does not have to be executed again via the UCServer.
- Optionally: "Public client/native (mobile and desktop)" "https://www.estos.de/piimt"
- Register the app.
- Under API Permissions, add the following Microsoft Graph permissions:
- Delegated permissions
- Presence.Read
- Presence.Read.All
- User.Read
- Application permissions
- Presence.ReadWrite.Al
- Delegated permissions
- Confirm the "Administrator consent".
It should look like this: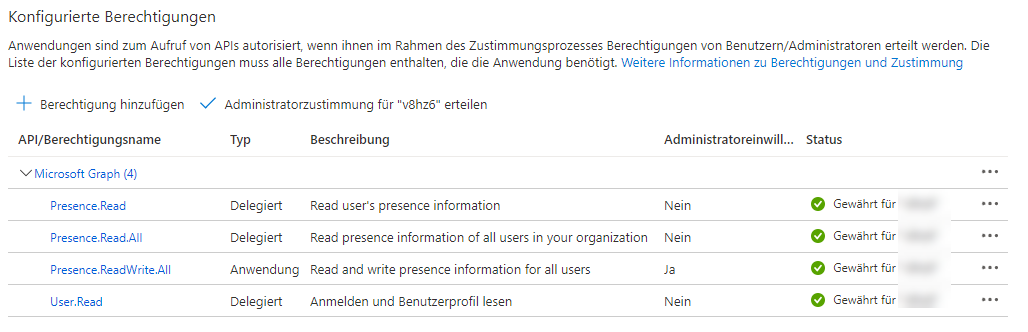
- Under "Certificates & privileges" you create a new private client key.
- Assign a description and a validity period.
- Copy the value immediately and save it. It can no longer be accessed via the portal interface.
- Observe the validity period and arrange for appropriate measures to be taken before expiry.
- Switch to the "Overview" tab and note:
- Application ID (Client)
- Directory ID
UCServer configuration
- Now connect to the server of your UCServer installation.
In UCServer Administration, make sure that "Integration with Microsoft Teams" is not enabled. - Exit the UCServer administration
- Optionally: If present, delete the following two files from the installation path of the UCServer installation:
- .\config\msteams.cfg
- .\config\msteams_auth
Create a new file msteams.cfg in the \config subdirectory of the UCServer installation with the following content:
{ "bEnabled" : 0, "bGetFromTeams" : 1, "bSendToTeams" : 1, "iLogLevel" : 4, "iPollingRate" : 5, "u8sTenant" : "Verzeichnis-ID (Mandant)", "u8sClientID" : "Anwendungs-ID (Client)", "u8sClientSecret" : "Clientschlüssel ", "u8sTokenCache" : "" }CODEComplete the value of u8sTenant, u8sClientID, u8sClientSecret according to your directory ID (client), application ID (client) and secret client key that you have noted down as described above.
If the value of u8sClientSecret changes due to renewal of the client secret key validity, then it can be replaced this way.
- Start the UCServer service again
- Restart the UCServer administration and follow the instructions: Start-up ProCall integration in Microsoft Teams.
Please adapt the instructions in all points when talking about app registration or company application.
It is no longer necessary to assign the admin consent, because you had already configured it via the Azure portal in the beginning.
Don't forget to assign user consent so that a working token is issued for authentication.