Requirement for Microsoft Graph Replicator in MetaDirectory – registration in Microsoft Azure-Portal
January 2022
Availability
The feature Microsoft Graph Replicator is available since MetaDirectory Version 5.0.12
Please take note of the product online help about Microsoft Graph Replicator.
And the hotfix notes for version 5.0.16: MetaDirectory 5.0.16: MetaDirectory 5.0.16 Enterprise Release Notes
The following steps in the Microsoft Azure Portal must be performed before the Microsoft Graph Import Replicator can be used in MetaDirectory:
Register the MetaDirectory application
App registrations
Navigate to the Microsoft identity platform for developers app registrations page
[ https://portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/RegisteredApps ].
- Select New registration.
- In the Name section, enter a meaningful application name that will be displayed to users of the app, for example, metadirectory-daemon.
- In the Supported account types section, select Accounts in this organizational directory only ({tenant name}).
- Select Register to create the application.
- Search for the Application (client) ID value in the app Overview page and note it down for later.
- Select the option New client secret in Client secrets on the Certificates & secrets page (left in the tree, see screenshot 1).
Sample Screenshot: Certificates & secrets under App registrations

- Type a key description (e.g. MetaDirectory secret),
- Select a key duration of either: In 1 year, In 2 years, or Never Expires.
When you press the Add button, the key value will be displayed. Copy and save the value in a safe location.
This key value will not be displayed again, nor retrievable by any other means, so record it as soon as it is visible from the Azure portal.
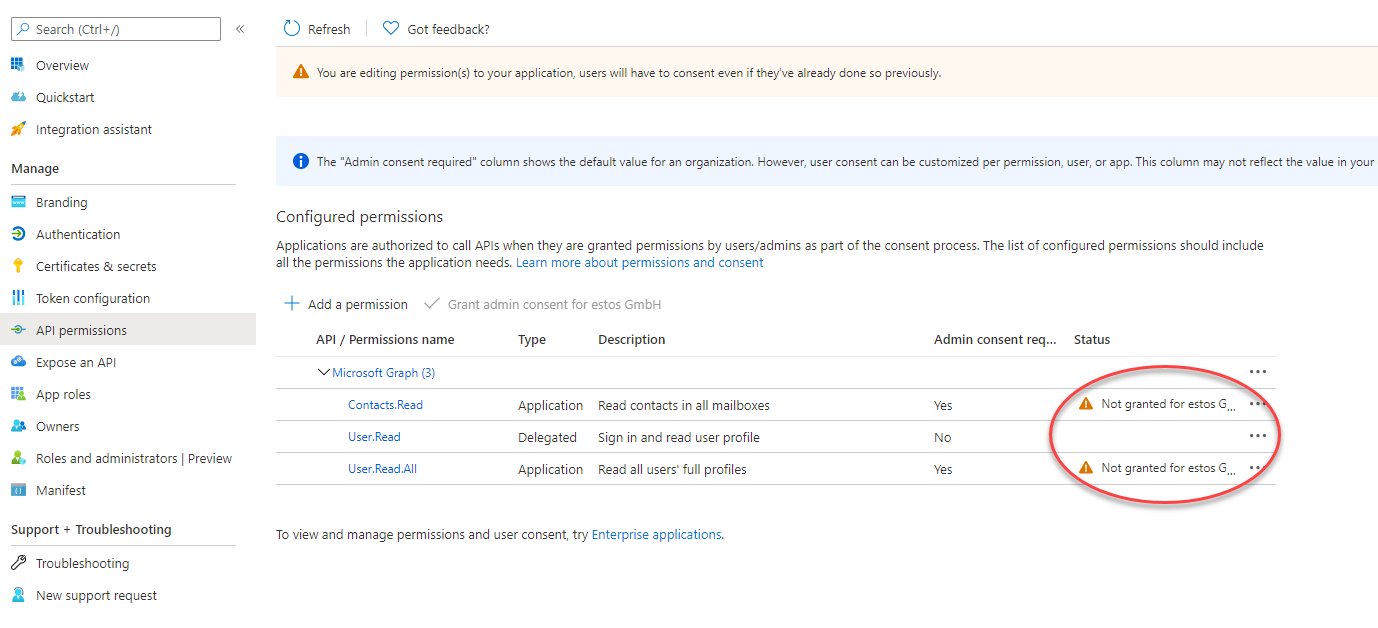
4. Select API permissions in the list of pages for the app,
- Click the Add a permission button and then,
- Ensure that the Microsoft APIs tab is selected
- In the Commonly used Microsoft APIs section, click on Microsoft Graph
- In the Application permissions section, ensure that the right permissions are checked: Contacts.Read and User.Read.All
Authorize accounts
Please see the note from Microsoft about the Azure Portal
The "Admin consent required" column shows the default value for an organization. However, user consent can be customized per permission, user, or app. This column may not reflect the value in your organization, or in organizations where this app will be used. Learn more
- Select the Add permissions button
At this stage, permissions are assigned correctly but the client app does not allow interaction. Therefore no consent can be presented via a UI and accepted to use the service app.
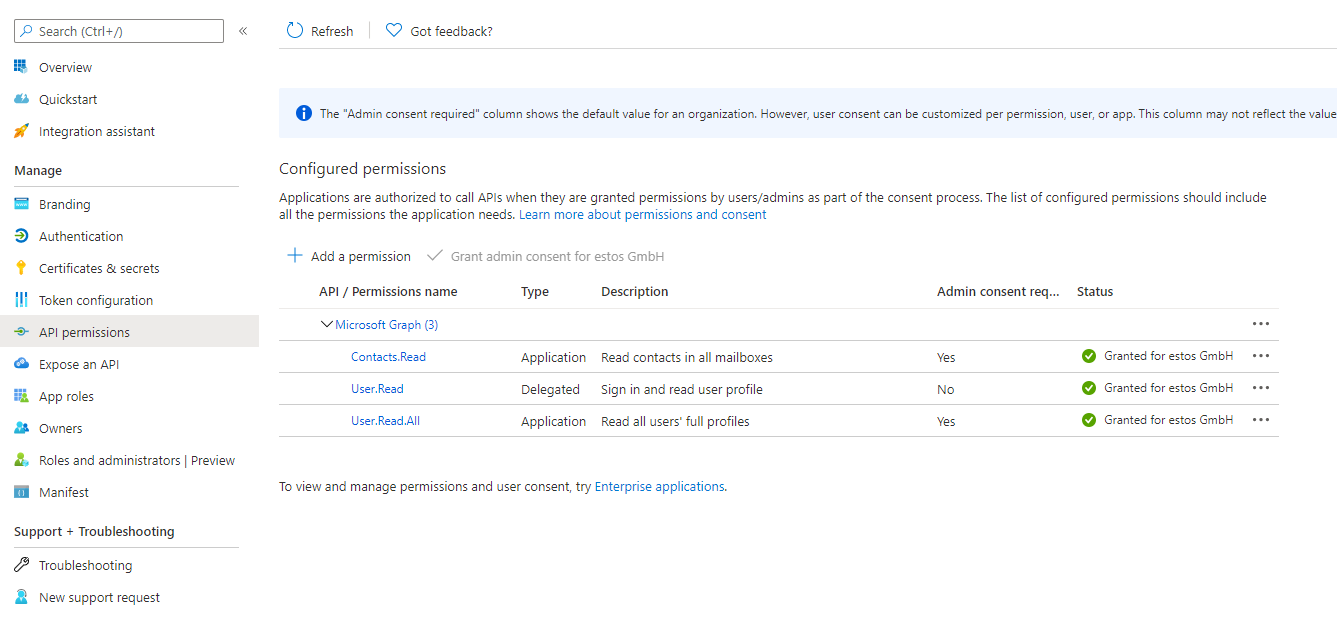
- Click the Grant/revoke admin consent for {tenant} button and Select Yes when you are asked if you want to grant consent for the requested permissions for all accounts in the tenant.
Authorisation required
You need to be an Azure AD tenant admin to grant permissions.